Complete Architecture Overview
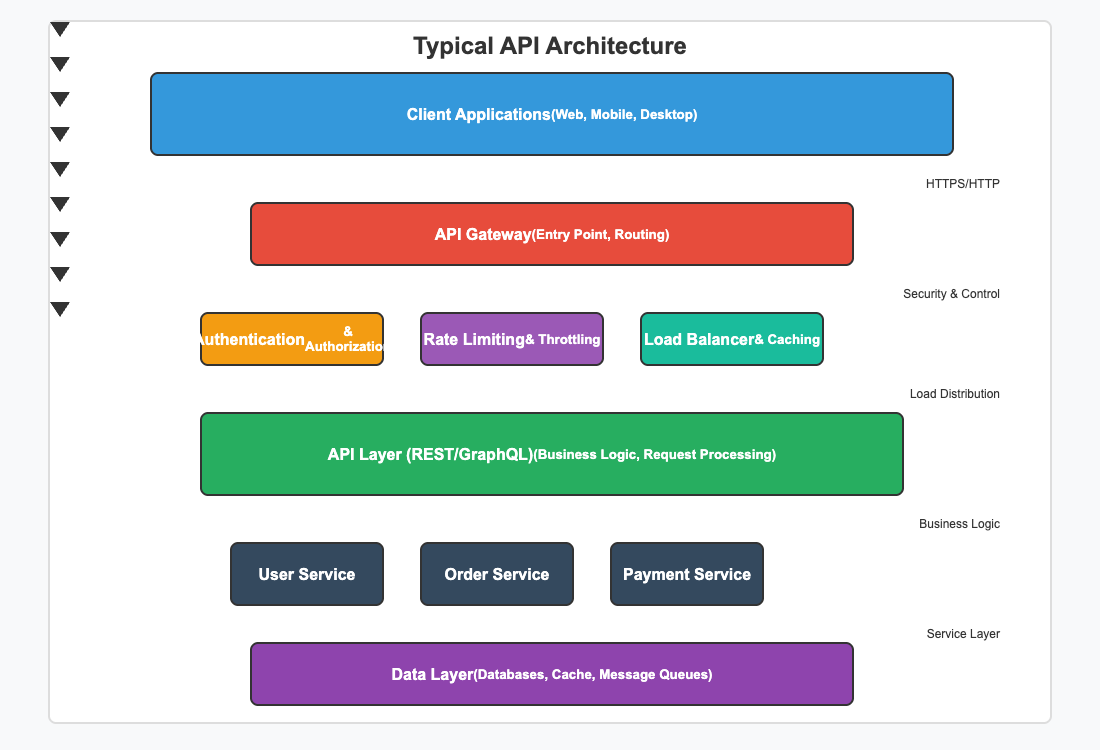
A comprehensive overview of modern API design patterns and architectural components

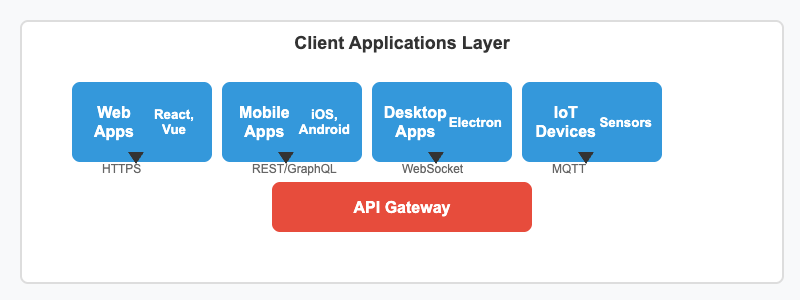
The top layer represents various client applications that consume the API services. These include web applications (React, Vue, Angular), mobile applications (iOS, Android, React Native), desktop applications, and IoT devices that need to interact with your API. Each client type uses different protocols and communication patterns optimized for their specific requirements.
Web applications typically use REST APIs over HTTPS, mobile apps may use GraphQL for efficient data fetching, desktop applications might use WebSocket for real-time communication, and IoT devices often utilize lightweight protocols like MQTT for resource-constrained environments.
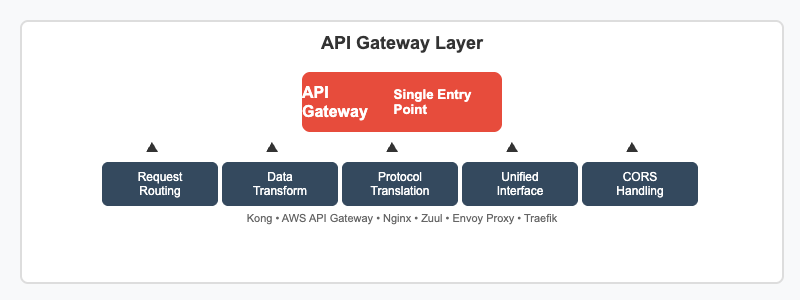
The API Gateway serves as the single entry point for all client requests, acting as a reverse proxy that routes requests to appropriate backend services. It handles cross-cutting concerns like request routing, protocol translation, request/response transformation, and provides a unified interface that abstracts the complexity of the backend architecture from clients.
Key functions include SSL termination, request aggregation from multiple services, API versioning, and CORS handling. The gateway can also implement API composition patterns, combining responses from multiple microservices into a single response for clients.

This critical security layer handles user authentication (verifying identity) and authorization (determining permissions). It implements industry-standard security protocols like OAuth 2.0 for secure authorization flows, JWT tokens for stateless authentication, API keys for service-to-service communication, and RBAC (Role-Based Access Control) for fine-grained permission management.
The layer supports various authentication methods including single sign-on (SSO) through SAML, multi-factor authentication (MFA) for enhanced security, and social login integrations. It also handles token refresh, session management, and security policy enforcement.
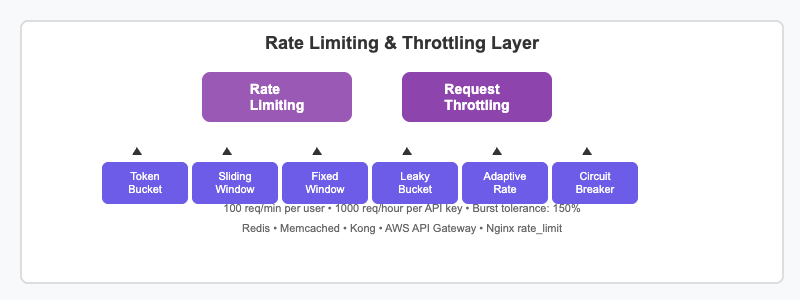
Rate limiting and throttling mechanisms protect your API from abuse and ensure fair usage among clients. Different algorithms serve various use cases: Token Bucket allows burst traffic up to a limit, Sliding Window provides precise rate limiting, Fixed Window offers simple implementation, and Leaky Bucket smooths out traffic spikes.
Advanced features include per-user limits, API key-based quotas, geographic rate limiting, and adaptive rate limiting that adjusts based on system load. Circuit breakers prevent cascade failures by temporarily blocking requests to failing services.
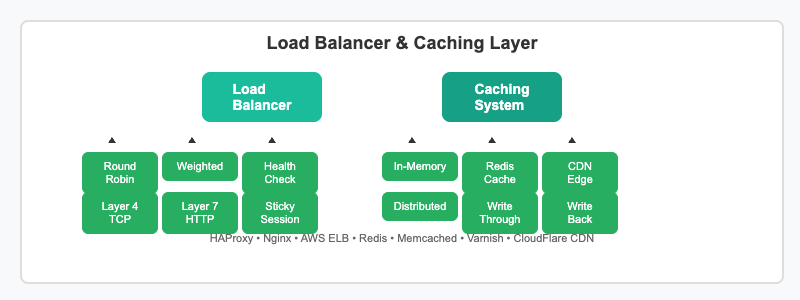
Load balancers distribute incoming requests across multiple server instances using various algorithms. Round-robin distributes requests evenly, weighted routing directs more traffic to powerful servers, and health checks ensure requests only go to healthy instances. Layer 4 load balancing works at the transport layer, while Layer 7 operates at the application layer with content-aware routing.
Caching dramatically improves performance by storing frequently accessed data. In-memory caches like Redis provide ultra-fast access, distributed caches scale across multiple nodes, and CDNs cache static content at edge locations worldwide. Cache strategies include write-through, write-back, and cache-aside patterns.
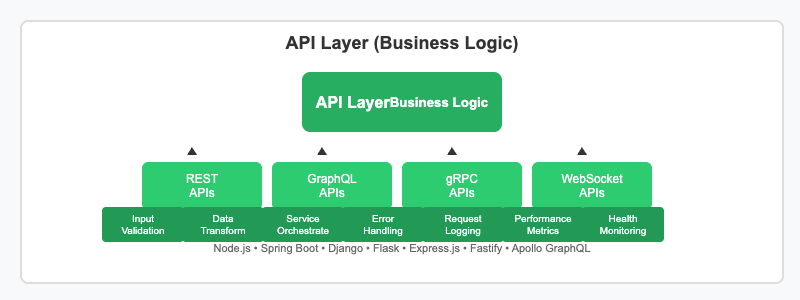
The core API layer implements business logic and handles request processing. It supports multiple API paradigms: REST APIs using standard HTTP methods for resource manipulation, GraphQL APIs providing flexible data queries and mutations, gRPC for high-performance inter-service communication, and WebSocket APIs for real-time bidirectional communication.
This layer orchestrates calls to various microservices, performs input validation, handles data transformation, implements error handling strategies, maintains request logs for debugging, collects performance metrics, and provides health monitoring endpoints for system observability.
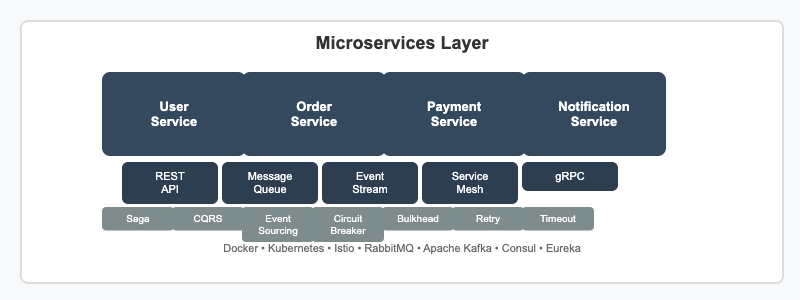
Individual microservices handle specific business domains with clear boundaries and responsibilities. Each service is independently deployable, scalable, and maintainable. Services communicate through well-defined APIs, message queues for asynchronous processing, event streams for real-time data flow, and service meshes for secure inter-service communication.
Key patterns include Saga for distributed transactions, CQRS for separating read/write operations, Event Sourcing for audit trails, Circuit Breaker for fault tolerance, Bulkhead for resource isolation, and Retry/Timeout patterns for resilience. Each service can use different technology stacks optimized for its specific requirements.
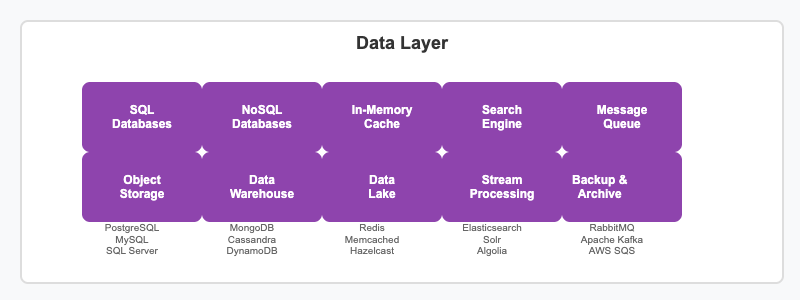
The data layer encompasses all data storage and processing systems. SQL databases provide ACID compliance for transactional data, NoSQL databases offer flexible schemas for various data models, in-memory caches enable ultra-fast data access, search engines power full-text search capabilities, and message queues facilitate asynchronous processing.
Advanced data architecture includes object storage for files and media, data warehouses for analytics, data lakes for big data processing, stream processing for real-time analytics, and comprehensive backup and archival systems. Different services may use polyglot persistence, choosing the most appropriate database technology for their specific data requirements.
Each layer can be scaled independently based on demand. Horizontal scaling is achieved through load balancers, containerization, and auto-scaling groups that automatically adjust capacity.
Multiple security layers including authentication, authorization, rate limiting, secure communication protocols, and defense-in-depth strategies protect against various attack vectors.
Separation of concerns makes the system easier to maintain, debug, and update individual components without affecting others. Clear boundaries enable team specialization.
Caching strategies, load balancing, optimized data access patterns, CDN utilization, and database optimization ensure high performance and low latency responses.
Redundancy, fault tolerance, graceful degradation, circuit breakers, and comprehensive monitoring ensure high availability and system resilience.
Modular architecture allows for technology stack diversity, easy integration of new features, third-party services, and adaptation to changing business requirements.
Start with a monolithic approach for small applications and gradually decompose into microservices as the system grows and requirements become clearer. This prevents over-engineering in early stages while maintaining the flexibility to scale architecturally as needed.
Implement comprehensive logging, monitoring, and distributed tracing across all layers. Use tools like Prometheus for metrics collection, Grafana for visualization, ELK Stack for log aggregation, and Jaeger or Zipkin for distributed tracing to maintain system health and debug issues quickly.
Plan for eventual consistency in distributed systems. Implement patterns like Saga for distributed transactions, CQRS for command-query separation, Event Sourcing for audit trails, and consider the CAP theorem implications when designing data storage strategies.
Maintain comprehensive API documentation using OpenAPI/Swagger specifications, implement automated testing at each layer including unit tests, integration tests, contract tests, and end-to-end testing. Use API mocking for development and testing isolation.
Implement security throughout the architecture with principles like least privilege access, defense in depth, regular security audits, dependency scanning, secrets management, and compliance with standards like OWASP API Security Top 10.
Optimize at every layer with strategies like connection pooling, query optimization, efficient serialization, compression, lazy loading, pagination, and performance budgets. Monitor key metrics like response times, throughput, and error rates continuously.